A SIM swap scam tricks your carrier into sending your texts and calls to a scammer — including password recovery and account verification codes. If a SIM swap cracks open your social media or bank accounts, it can have devastating consequences. Learn all about SIM swapping and how to avoid SIM swap attacks. Then install a comprehensive security suite to help protect against all types of online scams.
What is a SIM swap
A SIM swap fraud, also referred to as "simjacking" or "simcard hacking," occurs when malicious actors deceive a cellular service provider into transferring a victim's phone service to a SIM card under their control, effectively seizing control of the victim's phone number. The primary objective of a SIM swap is typically to exploit two-factor authentication methods and gain unauthorized access to bank accounts.
Every SIM card possesses a distinctive identifier, which mobile networks use to validate subscriptions to service providers like Vodafone or O2, and to route phone calls and text messages to the correct mobile device. However, in the event of a SIM swap, the victim's mobile account becomes associated with a different SIM card, redirecting all incoming network traffic to another location.
This type of identity theft frequently stems from cybercriminals successfully phishing for the victim's personal information. An essential precautionary measure to thwart identity theft, particularly sim swap fraud, is to acquire the knowledge of how to block spam text messages.
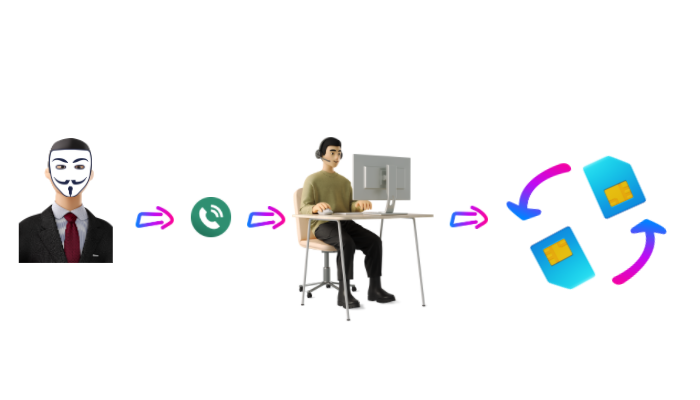
A SIM swap scam happens when a fraudster convinces a service provider to switch a victim’s service to a SIM card that they control.
How SIM swapping works
For a SIM swap attack to work, scammers need to successfully impersonate a victim and convince their mobile carrier to transfer their mobile service to another SIM card. To do this, they usually claim that the original SIM card has been lost, stolen, or damaged, and they provide sensitive personal information to “prove” their identity.
These details may be bought through data brokers, found in data breaches on the dark web, or even stolen using spyware. Another information-gathering tactic is a version of phishing called smishing, where SMS messages are sent by hackers purporting to be reputable companies.

To execute a SIM swap attack, a hacker may first phish for personal information.
A 2020 Princeton University study1 of social engineering ploys used to fool cellular service providers showed the following details to be most critical:
- Financial information: Details on the credit card attached to the account, such as the last four digits, the date of activation, the last payment, and especially the CVC (card verification code) on the back.
- Device details: The IMEI (International Mobile Equipment Identity), which is your device’s unique serial number, or the ICCID (Integrated Circuit Card Identifier), which is your SIM card’s unique serial number.
- Personal data: Your billing address, full name, date of birth, or even just your email address.
- Call logs: Any recently dialled numbers, dates of calls, or the identities of call recipients.
- Account credentials: Confidential authenticators such as PINs, passwords, and answers to security questions.
- One-time passcodes (OTPs): These fall under items only you should “possess,” and are another factor in two-factor authentication.
After a SIM swap, the scammer can then access any accounts that use your phone as a second factor in two-factor authentication (2FA). Usually, this verification method is secure, but if a SIM swapper has compromised your phone number, they can have account password reset codes sent to their device, and lock you out of your social, banking, and other online accounts.
1 https://www.usenix.org/system/files/soups2020-lee.pdf
Signs that you're the victim of a SIM swap attack
If you know the signs to look out for, timely SIM swap detection may allow you to minimize the impact of a SIM swap attack that’s already underway.
Here are the major red flags to look out for:
You can't make calls or send texts
If you’re unable to make calls, texts, or use mobile data, that’s a sign that something’s seriously wrong with your network connection. The problem could be a simple service outage, or it could be because a SIM card swap has transferred your cell service and phone number to somebody else.
You're notified of activity elsewhere
Many services will notify you if they detect unusual account activity. If you start getting emails about suspicious activity on your accounts, there might be a SIM swap hack in progress. Likewise, your cell carrier may send you a confirmation message that your phone number has been activated on a new device.
You're unable to access accounts
A SIM card hackers’ first move is often to lock you out of your accounts by changing the passwords. Some accounts also will also automatically block access as a security measure after too many questionable login attempts. So, losing access is a clear signal that someone has — or is attempting to — compromise your accounts, and you should take immediate steps to secure them.
You find unauthorized transactions
The ultimate goal of a SIM swap attack is often to drain a victim’s bank account. If you get notifications about transactions you didn’t make, it could be due to SIM swapping. In this case, as well as disputing the unauthorized charges and securing your financial accounts, it’s vital that you regain control of your phone number as soon as possible.
What to do if you're the victim of a SIM swap scam
If you think you’ve been SIM swapped, act quickly to prevent further hacks. To regain control of your financial accounts and mobile carrier service, follow the steps below:
1. Contact your cell provider
Contact your cell provider as soon as possible if you suspect a SIM swap. Your cellular service provider may not be able to catch the crook, but they can put an end to their scheme by cutting off their access to your mobile network.
With so much at stake, networks must respond quickly when they discover a customer has fallen victim to a Sim-swap attack.
No network offers a 24/7 customer services telephone helpline, although EE, Plusnet, Tesco Mobile and Vodafone told us that an out-of-hours support team can still place restrictions on your account to block unauthorised access.
If you're with Virgin Media, it has an online form used to report lost or stolen devices, which will temporarily block your Sim. Three offers 24/7 webchat.
O2 said that any customer who suspects they're a victim of fraud should immediately contact their bank and O2 as soon as possible from another phone.
Sky Mobile wasn't able to provide answer if it can address such issues.
2. Secure your financial accounts
Next, contact your bank to advise them of the situation. Their support team will walk you through what you need to do to protect your finances, but you should certainly freeze your accounts to block all transactions until you’re sure they’re secure. If unauthorized transactions have already gone through, start the dispute process to see if they can be cancelled or refunded.
With smartphones providing a gateway to our financial data, the banking and telecoms industries should consider how to take a more collaborative approach to tackling Sim-swap fraud.
In Mozambique, mobile networks now flag to banks mobile phone numbers associated with recent Sim ports.
Banks can block transactions if the number has been ported within the previous 48 to 72 hours - enough time for the original owner to contact their network provider if they discover they have fallen victim to an unauthorised Sim swap.
While this may frustrate customers who have legitimately ported their Sim card and don't want payment delays, banks can potentially find other ways to verify the request is genuine. In any case, customers should be able to decide whether this is a compromise they are willing to make.
3. Disable 2FA and change your passwords
Until you’re 100% certain the SIM swap scammer no longer has access to your texts and calls, prevent them from locking you out of any more accounts by logging in, disabling 2FA in your account settings, and then choosing a new, strong password for good measure.
As well as re-enabling 2FA once your cell service is restored to a SIM card you control, make sure you have all account security features and notifications turned on to help you detect and prevent SIM swap attacks and other hacks in the future.
How can you prevent SIM swap scams?
Many SIM swap protection tips are the same as for avoiding Amazon scams, tech support scams, and other generic ploys designed to compromise your personal information and access your devices. But there are specific actions you can take to help prevent SIM swap 2FA hacks.
Here’s how to protect against SIM swap fraud:
Modify online behaviour
Simjacking scammers cyberstalk their targets before they strike. Every piece of information you post can be used to build your identity profile. Never post your address or phone number and avoid disclosing your full name and birth date. You should also be careful when sharing personal details that only you should know.
Don't reply to calls, emails, or texts requesting personal info
Legitimate institutions will never call you and request your private details. Scammers might try to pose as your service provider, a bank, or even the government to trick you into giving up personal info. SIM hackers also often use SMS messages to seek information or trigger malware.
Enhance account security
To secure your apps and accounts, consider using biometric authentication such as Face ID as a more secure 2FA factor. Also check out the best password managers, which can help keep your passwords unique and complex.
Use PIN codes
Be sure to change your phone’s default SIM pin by manually setting a PIN or password on your SIM through your phone’s settings. Many carriers now offer Number Transfer PINS as well, which come into effect when a SIM change is requested. This means if someone tries to SIM swap you, they’ll need your PIN first — no matter what other details they possess.
Build IDs without your phone number
Some companies like Yubikey2 offer hardware authentication factors that are not linked to your SIM card or phone number. You enter your username and password like usual. But instead of getting a text, notification, or phone call to verify yourself, you press a button on the plugged-in device, which has a unique identifier.
Set up bank and mobile carrier alerts
You can request notification emails or text messages to alert you to any changes to your bank or cell carrier accounts. This acts as an early-warning system that can help you detect and prevent SIM swapping attacks and other fraudulent activity before any damage is done.
Go phoneless
If an account is particularly sensitive or is a likely target for scammers, consider linking it to a no-contract, temporary phone (also called a burner), or just not linking it to a phone at all. It may be a bit more hassle on your end, but the peace of mind you get from knowing you are protected from SIM swapping and other scams could be worth it.
Authentication Apps
Instead of authenticating through your phone service, authenticate through apps such as Google Authenticator, which cannot be transferred to other devices, and are themselves protected by an extra layer of security such as a PIN or biometric factor. That makes it harder for hackers to exploit, even if you lose a phone with Google Authenticator on it.
Social media's role in SIM swap fraud
Scammers and fraudsters lurk on social media to discover as much as they can about their potential victims. Instagram scams often use fake profiles to get personal details through direct messages, while sugar daddy scams and other romance scams feign romantic interest to seek out credit card numbers, high school backgrounds, or other unique information.
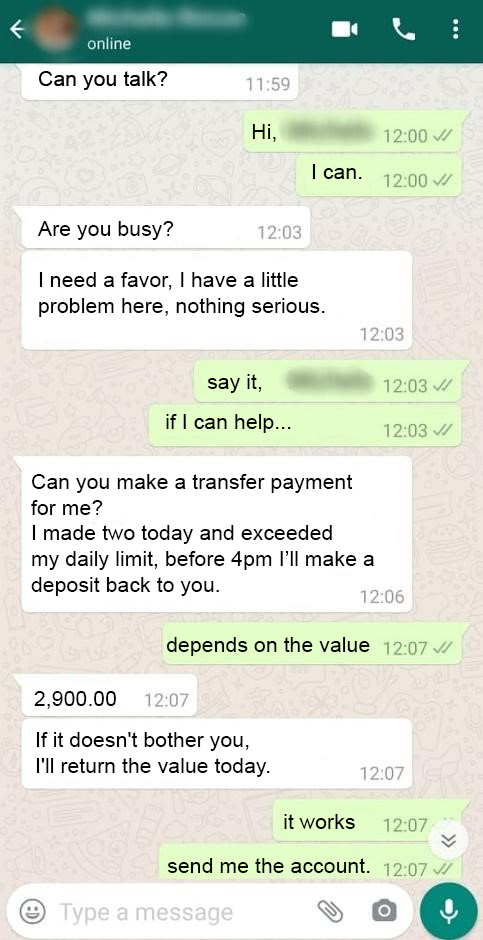
An example of a SIM scam text.
Are SIM swap scams on the rise?
SIM swap scams are a significant online risk. In November 2022, the FBI even warned about SIM swaps3, claiming that in the previous year over $68 million was estimated to have been lost in SIM swap scams.
3 https://www.ic3.gov/Media/Y2022/PSA220208
Secure your SIM card from swapping attacks
Fraudulent schemes like SIM swaps often start slowly, with scammers gradually harvesting your personal information, before escalating into attempts to hack into your devices and accounts.
Internet security centre’s help defend against the scams that hackers may use in subsequent SIM swap attacks by providing comprehensive security and privacy protection. These security solutions block malware, phishing links, and fake websites. And can include a built-in VPN to encrypt your connection and help keep your personal data safe online.
FAQs
How do SIM swaps work?
SIM swaps work by a hacker convincing a cell phone carrier to switch a mobile number to a SIM in the hacker’s possession. After gaining control of the phone number, the hacker can change the passwords to all the accounts that use that number for two-factor or multifactor verification.
Is SIM swapping a crime?
Yes, SIM swapping is a cybercrime involving identity fraud, computer fraud, wire fraud, conspiracy, and theft. SIM swapping is a serious cybercrime that carries severe penalties, including decades of prison time.
What is a SIM card swap hack?
A SIM card swap hack is another name for a SIM swap. In a SIM card swap hack, a victim’s cell phone service is fraudulently transferred to another SIM card. A SIM card can also be cloned physically with a card reader.
Can you prevent a SIM swap?
Yes, you can help prevent a SIM swap by using complex and unique passwords and keeping any personal information off of social media. SIM swaps prey on easy-to-guess passwords and private details in order to trick cell service carriers they are a paying customer. Authenticator apps like Google Authenticator and physical security keys like Yubikey also greatly increase SIM swap prevention.
How long does a SIM swap last?
A SIM swap lasts as long as the SIM swapper goes undetected, or when they decide to shut down service so as not to get caught. Usually, a SIM swap ends after the SIM swapper makes a big purchase or transfers a large amount of funds to a safe location.
ACE-CSE

Queen’s holds an Academic Centre of Excellence in Cyber Security Education (ACE-CSE) Gold Award from the National Cyber Security Centre (NCSC) and the Department for Science, Innovation & Technology (DSIT).